Watch Out for These Twists on Phishing
- Details
- Written by Remar Sutton
- Category: Articles

If you have been online for any length of time, you have heard about phishing. Phishing uses a variety of methods to obtain your personal and financial information which can then be used to steal your money and your identity. Phishing scams typically try to get you to act quickly without thinking and they are getting harder to spot.
Phishing will continue to get harder to detect. Take steps now to reduce your chances of getting caught.
Phishing Methods
While phishing has usually used email, it has spread across devices and is using additional methods. Some phishing attempts combine various methods. Some of these methods include:
Text messaging, called smishing. Phishing texts typically have a link to a website that tries to collect your information. These texts are designed to grab your attention and seem to need an immediate response.
Voice phishing, called vishing. Phishing phone calls typically fake the Caller ID information. The caller may ask for specific information, give you a phone number to call or a website to visit. They are designed to get you to act quickly.
Mobile phishing. Detecting phishing is much harder on mobile devices. Links can't be easily validated by hovering over them. URLs are truncated in mobile browsers. Apps such as messenger services and social media can be used in phishing attacks. Fake apps can mimic popular brands and companies.
Spear phishing. This is a form of phishing that targets an individual or group of individuals with a personalized message using information that is available on the internet. Phishers collect that information from social media sites, websites and data breaches.
Ads. Clicking on a link in an ad could take you to a fake site or cause malware to be loaded on your device.
Social media. Phishers gather information from social media in multiple ways. They use private messages with a shortened link for a website to collect your information or get you to download malware. They sometimes pose as a person and eventually get you to reveal detailed information. They collect information from profiles even if your profile is set to private since they have tools that they can use to access the data.
Fake websites. Phishers will clone popular websites and use a misleading web address in order to collect your information.
Examples of Phishing Scams
Phishing can take many forms. Here are just a few examples of the fake ploys that appear to be real.
-
Notification from your financial institution such as your credit union, bank, or credit card company. The message provides some reason why you need to log in to your account (statement ready, suspicious activity, action required, message) and provides a link. The link goes to a cloned site which will collect your login information.
Notification that you've been locked out of your account. You are asked to provide information or verify an action through the provided link in order to unlock your account. The link goes to a cloned site which will collect your login information.
A job offer, recruitment pitch, job description, or resume with an attachment or link. The attachment probably will infect your device with malware. The link goes to a fake website which will collect your personal information.
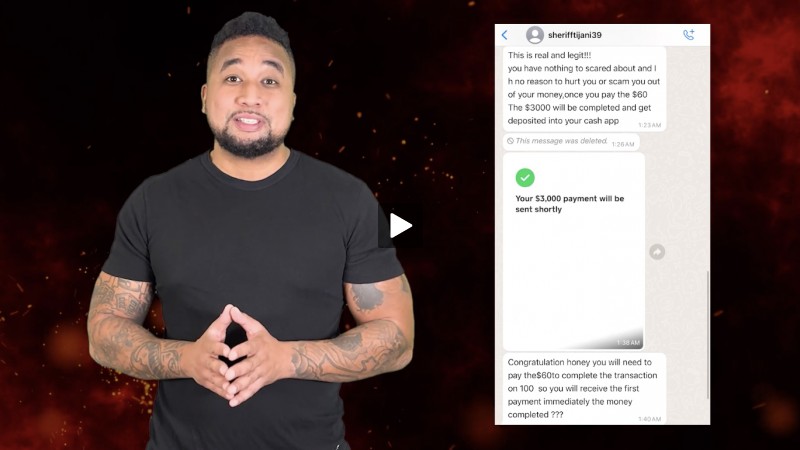
Request for a donation with a link or phone number to call. Your financial information will be collected over the phone or through a cloned site. The phisher typically uses a name similar to a well-known charity.
Notification that you have won a prize or that you are owed a refund with a link. The link goes to a fake website which will collect your personal information.
A warning from the IRS, collection agency, or government agency stating that you owe money and threatening legal action or arrest is you don't pay. Your financial information will be collected over the phone or through a fake website.
Confirmation of an order or delivery information with a link. The link goes to a cloned website which will collect your personal information.
Request from a friend or co-worker to review a document or check out a website. The attached document be malware. The link goes to a fake website.
As these examples show, any message can be a phishing scam. You can test your phishing knowledge by taking this Phishing IQ test from SonicWall.
How to Avoid Being Caught
There are precautions that you can take to avoid phishing scams. These tips can help.
Take your time. Don't rush even if the message seems urgent. Phishers like to play on your emotions.
-
Even though phishing is harder to detect, poor spelling and grammar can still be a red flag.
Don't click on links no matter who sent them. Go to the website by typing the address in your browser or search for the web address. Use a bookmark if it is site you frequent. Shortened or odd looking web addresses can be a red flag.
-
Don't send personal or financial information in an email or text message.
-
Make sure that a website is secure before submitting personal or financial information. Verify that the security certificate matches the website address by clicking on the lock icon. Some browsers and security software will warn you if there is an issue with the certificate.
-
Use security software including firewalls. Take advantage of the security features in your browser and email program including anti-phishing tools. Use the security features provided by mobile operating systems and carriers.
-
Keep your browser and operating system up to date. Installing updates when they are available will close the loopholes that phishers and other hackers exploit.
-
Only open attachments that you are expecting, even if it comes from someone you know. Verify that they sent it before you open it.
-
Check the sender address or phone number. For example, a sender address that doesn't match the web address or a text message that comes from an unknown number or sender.
Limit the amount of information you provide about yourself online and limit where you share it.
Protect your accounts by using two-step authentication where available. This type of authentication requires more than a password to access your account such as a code sent to your phone.
Phishing will continue to get harder to detect. Take steps now to reduce your chances of getting caught.